Photo by Micah Williams on Unsplash
AWS ACM PCA
ACM Private CA enables the creation of private certificate authority (CA) hierarchies, including root and subordinate CAs[2].
What is a certificate authority (CA)?
A certificate authority (CA), also sometimes referred to as a certification authority, is a company or organization that acts to validate the identities of entities[1]. There are many companies in the world that are CAs. You can buy services from them and use them to enable HTTPS in your websites among other things.
In your Browser's address bar, there is a padlock icon and by clicking on it you can see the CA for the certificate that is being used by the website you are in.
 |
| Figure 1: CA |
The above diagram shows the root CA(Google Trust Services - GlobalSign Root CA-R2) for the blogger.com platform. These certificates were provided by a company called GlobalSign.
You will also see that there are three certificates in the image in a hierarchical structure. More about that can be found in the next section.
Certificate authority (CA) Hierarchies
In large organizations, responsibility for issuing certificates can be delegated to several different CAs[5].
 |
| Figure 2: CA Hierarchies(source: Redhat) |
The root CA's certificate is a self-signed certificate that is maintained by a Company such as GlobalSign. Subordinate CA's certificates are signed by the root CA while these Subordinate CAs can sign other Certificates which forms a hierarchy(Figure 2).
According to a report that was created about the 2011 DigiNotar incident[6], companies have implemented many security measures to protect the root certificates. If the root certificate got compromised somehow, hackers can issue certificates to other parties that could use those certificates for hacking.
This incident happened in 2011 led to the Certificate Transparency project. More about this later.
More about AWS ACM PCA
There are companies out there like GlobalSign where you can buy Certificates for your needs. With AWS ACM PCA you can create your own root certificates under your name or company name without the costs of operating an on-premises CA.
The above video explains how to create a Private CA and use that to secure your website with HTTPS.
Whenever you import certificates to AWS Certificate Manager from ACM PCA, It publishes the certificates to CT logs on issuance and on renewal, unless you disable Certificate Transparency logging[7]. Browsers such as Chrome uses these CT logs to validate the certificates.
Certificate Transparency
Google's Certificate Transparency project aims to safeguard the certificate issuance process by providing an open framework for monitoring and auditing HTTPS certificates[4]. There are more than 12 billion certificates in these logs as of today(2021-02-08). All the certificates issued by companies including AWS ACM PCA are logged in these logs in order to be trusted by the web browsers.
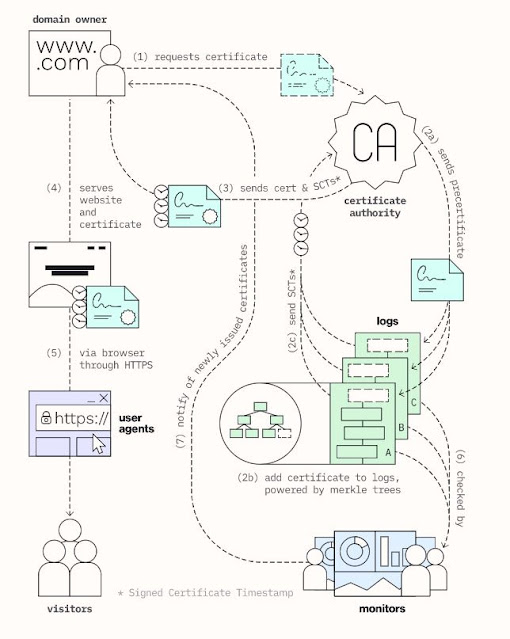 |
| Figure 3: How CT logs work (source: https://certificate.transparency.dev/howctworks/) |
ACM PCA for AWS IoT
IoT Devices use X.509 certificates to perform mutual authentication with AWS IoT[8]. Before start using your IoT devices via AWS Services, the device needs to be provisioned first. AWS Just-in-time registration(JITR) is a great tool to connect and initialize IoT devices with AWS IoT.
Just-in-time registration registers a device with AWS IoT when it connects for the first time [9]. During this process, a certificate, together with a policy will be created for the device to handle Authentication and Authorization for the device.
In order to support multi-region for your IoT infrastructure, you have to bring your own certificate to AWS IoT instead of certificates issues by AWS IoT[10]. In order to bring your own certificates, you can use AWS ACM PCA.
 |
| Figure 4: AWS IoT JITR (source: https://github.com/aws-samples/iot-provisioning-secretfree) |
ACM PCA for SSL Pinning
- Import a certificate that you bought from another company to the AWS Certificate Manager (ACM) and do SSL Pinning.
- If using public certificates, pin to all available AWS root Certificates not to the ACM certificate itself because those are renewed automatically by ACM. Automatic renewal could break your app integrations.
- Use AWS ACM PCA to create a private CA and import the certificate to ACM. Use the imported certificate to do SSL pinning.
Example
References
- https://docs.aws.amazon.com/acm-pca/latest/userguide/PcaWelcome.html
- https://www.ssl.com/faqs/what-is-a-certificate-authority/
- https://certificate.transparency.dev/howctworks/
- https://transparencyreport.google.com/https/certificates
- https://access.redhat.com/documentation/en-us/red_hat_certificate_system/10/html/planning_installation_and_deployment_guide/introduction_to_public_key_cryptography-certificates_and_authentication#Certificates_and_Authentication-How_CA_Certificates_Establish_Trust
- https://slate.com/technology/2016/12/how-the-2011-hack-of-diginotar-changed-the-internets-infrastructure.html
- https://aws.amazon.com/blogs/security/how-to-get-ready-for-certificate-transparency/
- https://docs.aws.amazon.com/iot/latest/developerguide/iot-provision.html
- https://iot-device-management.workshop.aws/en/provisioning-options/just-in-time-registration.html
- AWS re:Invent 2018: Implementing Multi-Region AWS IoT, ft. Analog Devices (IOT401) (https://youtu.be/vq7m1IUjxdk)
- https://github.com/aws-samples/iot-provisioning-secretfree
- https://docs.aws.amazon.com/acm/latest/userguide/acm-bestpractices.html#best-practices-pinning
- https://developer.mozilla.org/en-US/docs/Web/HTTP/Public_Key_Pinning
- https://square.github.io/okhttp/4.x/okhttp/okhttp3/-certificate-pinner/
- https://www.charlesproxy.com/

ok
ReplyDeleteWith OneSimCard’s IoT checking dashboard, you look at real-time or noteworthy activity volume by gadget or by sending. This makes a difference you distinguish anomalies in information utilization and superior get it you every day and month-to-month activity standards. You'll moreover set benefit volume limits to anticipate too many tall bills. Roaming IoT SIM Card
ReplyDeleteRather like Facebook and Twitter, including perfect hashtags in your post captions can assist you in naturally constructing a strong group of onlookers base and make your recordings more discoverable on TikTok. Buy TikTok Accounts
ReplyDeleteThis implies that you can make and receive calls from anywhere worldwide using your local SIM. However, the main drawback is the expensive incoming and outgoing call rates they charge for their roaming service. IoT SIM Card
ReplyDelete